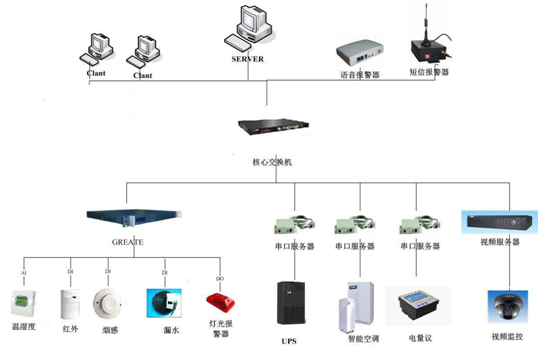
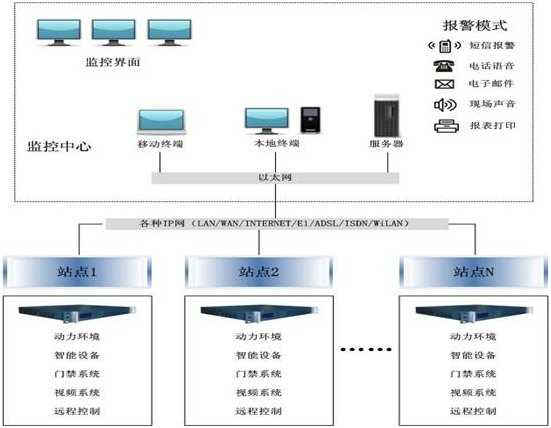
The ETMAN computer room power environment monitoring system is a highly reliable, stable, and modular intelligent data center infrastructure monitoring system. It targets equipment such as UPS, precision air conditioning, water leakage, temperature and humidity, security, access control, fire protection, smoke sensors, etc. Through communication interaction, intelligent analysis, intelligent control, and humanized display methods, the data center operation and maintenance personnel can timely understand the health status of the data center, Create a new type of green and energy-saving computer room.
Architecture of ETMAN Computer Room Power Environment Monitoring System
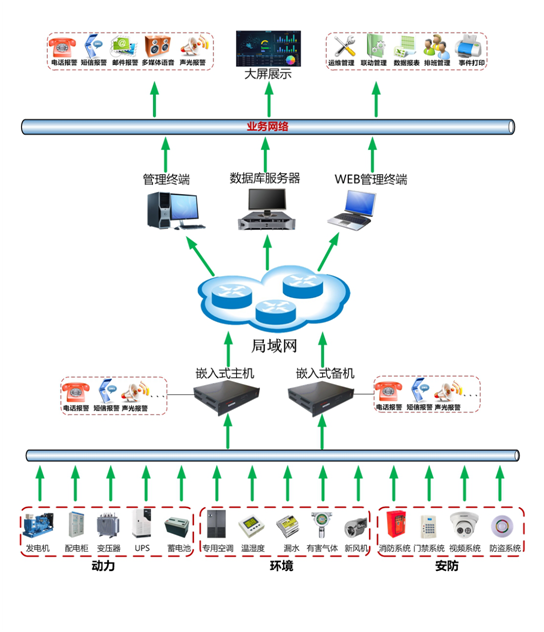 System advantages
System advantages
Stability and Safety
This system adapts to the development trend of digital and networked monitoring, and does not lag behind or duplicate investment; Using internal enterprise LAN or WAN communication and management to ensure stability and security. By using TCP/IP, each monitored computer room can easily establish connections with the monitoring management center and database, and monitor the power equipment, computer room environment, security and fire protection, video images, and other information of the monitored computer room under a unified platform at a lower cost.
Real time and scalability
The monitoring host adopts an integrated design of collection, analysis, transmission, and alarm, with fast alarm, timely data display, complete data recording, and intuitive data analysis; The system is designed in a modular manner and has openness. It can flexibly build monitoring systems of various scales and connect with internal network systems of the enterprise. Regardless of the network transmission method, it can be organically integrated into a whole, which will be important. There are significant differences in the size of computer rooms, and it is required that the designed system be suitable for various practical situations, have strong scalability, and can adapt to the expansion requirements of the system at any time.
|
System Type |
2D/3D |
|
Networking |
The device follows the TCP/IP protocol and is suitable for online monitoring. It can complete monitoring of computer room security without the need for dedicated devices |
|
cost performance |
tall |
|
structure |
Embedded structure |
|
open |
Standard XML parsing simple language, convenient for secondary development |
|
Software architecture |
B/S architecture, monitoring is as convenient as accessing the internet |
|
Remote management maintenance |
IP-based management, which can be configured, managed, and maintained remotely through the network |
|
energy consumption |
Less than 20W |
|
Incoming call self start |
When there is a power outage and a call is made again on the unmanned site, it can be started by itself |
|
Host operating system |
Embedded real-time operation (RTOS and embedded LINUX) |
|
Host built-in functions |
Built in WEB server, WYSIWYG |
|
Dual data flow |
Monitoring data can be simultaneously transmitted to two management servers |
|
apply |
Various industries |
|
expand |
Ready to install and use |
System characteristics
Highly centralized management
The system is based on TCP/IP and SNMP, with a highly centralized management concept. It can not only comprehensively monitor various status information, alarm information, control commands, and historical data of various power and environmental equipment in a single computer room, but also achieve cross regional centralized monitoring of multiple computer rooms distributed throughout the country.
Flexible remote management
The system can not only achieve local management of monitoring, but also provide highly reliable remote management. Managers can remotely view the operation of devices and systems in each computer room on any terminal through web browsing on the Internet. If permissions allow, they can also control and manage devices and systems.
Powerful alarm handling
The system can distinguish multi-level alarm levels and set alarm levels according to user needs. When an alarm event occurs, the system automatically queues up alarms and processes them according to the event level, and sends alarm information corresponding to each level; The system provides a variety of alarm methods for users to choose from, including computer screens, multimedia voice, phone calls, mobile text messages, and emails. When an alarm event occurs, it ensures timely notification of the alarm situation; The system can also provide location-based alarms for alarms distributed in different areas and devices through intelligent voice combination, facilitating managers to accurately understand the location and status of the alarm situation, and achieving unmanned or fewer people on duty in modern computer room management.
Powerful data management
The system automatically records complete information such as operators, operation content, operation time, fault points, fault content, fault handling, and fault time. It provides two query methods: real-time dynamic curve and historical curve, making it convenient for managers to quickly analyze the system's operation status through intuitive graphical display, providing complete system operation and maintenance information for managers. The system is embedded with a powerful report management system, which can provide commonly used daily reports, weekly reports, and monthly reports.
Reliable security management
The system has powerful permission management functions, which can assign different operation permissions to managers and users, and group all managers and users according to their functions to prevent system information leakage and interference by unauthorized personnel.
High reliability of the system
All hardware equipment of the system is industrial control equipment, and the signal processing interface board has an average time between failures of over 200000 hours. The module adopts a fully sealed structure and solid-state packaging, with extremely high reliability. The central monitoring equipment adopts embedded LINUX system software, which has strong antivirus capabilities.
Friendly human-machine interface
The system provides electronic map display, which can fully digitally and realistically simulate the equipment environment layout and operation status of each machine room, so that the operator can see it at a glance. Real time dynamic display of parameters, with fully Chinese interface.
Powerful intelligent linkage
The system can achieve fully automated linkage control of relevant equipment or subsystems (such as controlling access control after the fire protection system alarms, and recording on-site images with adjacent cameras), improving the operational efficiency of equipment and subsystems and avoiding human delays in operation.
Strong compatibility
The system supports UPS such as MGE, EXIDE, LIEBERT, APC, BORRI, as well as precision air conditioners for computer rooms such as STULZ, HIROSS, LIEBERT, RC, ATLAS, ISOVEL, and various intelligent devices produced by other major manufacturers.
Powerful expansion function
The use of this system software and modification of the monitoring system do not require professional software knowledge. Users can freely modify the monitoring system due to changes in the computer room (equipment location, type, graphics, computer room structure, etc.) or the addition of equipment (within a limited range) or the increase of monitoring points.
Open interface
The system defaults to providing users with rich controls and libraries. If users have special industry needs, they can customize development controls and libraries according to their requirements. The customer system has no restrictions on these extensions, and the basic structure does not need to be changed.
Advanced and mature system
The system is fully designed and operated according to industrial standards, with monitoring software reaching the domestic level and cost-effectiveness reaching the international level. It has been widely used throughout the country.
System composition
It mainly includes three parts: monitoring device, transmission channel, and monitoring center. Among them, software architecture is composed of topology, and one monitoring management center can manage at least 200 unmanned machine rooms at the same time.